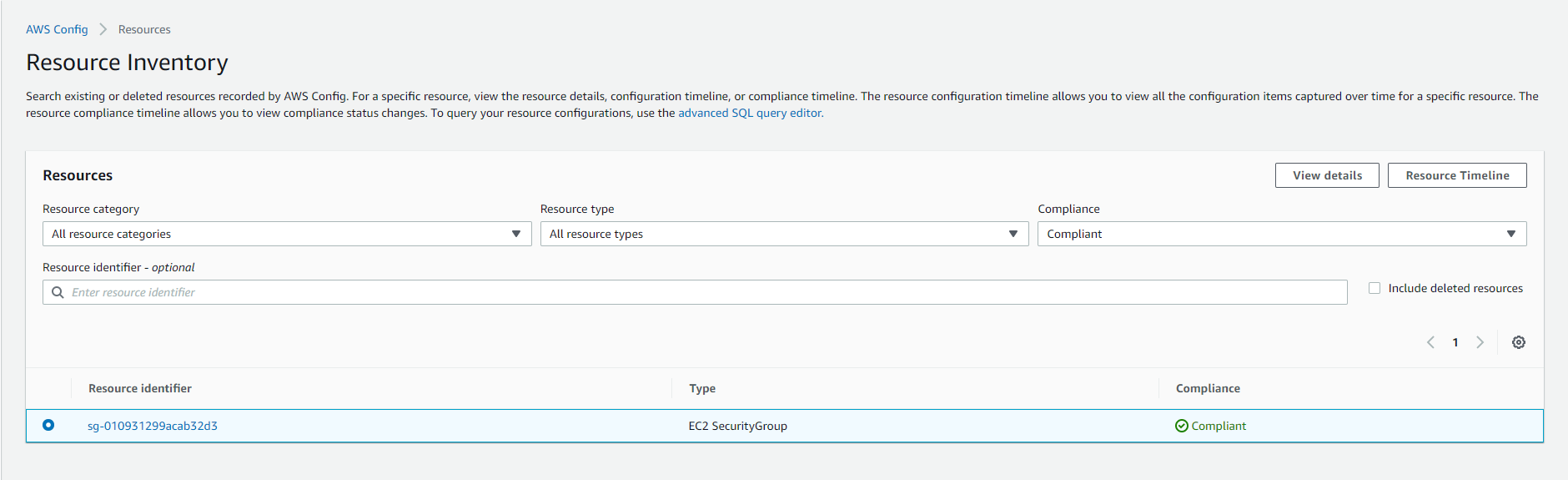
Security Groups
Get to know Security Groups
Security Groups is a potent tool created to manage network access to AWS Cloud resources, especially EC2 instances, thereby enforcing network security in the L3/4 layer but for EC2 interfaces.
Basic knowledge
Basic things we should know when conducting configuration:
- By default, there will be two rules: inbound and outbound.
- By default, there will not be any inbound rules that allow access in the incoming direction.
- It is not possible to create a rule with a negation rule.
- When associated with an EC2 instance will act as a
Host-based Firewall. - One EC2 instance can be associated with up to 5 Security Groups.
- Cannot link to a VPC or VPC Subnet.
- For regulation, the source can be:
- IP Address
- VPC Subnets CIDR
- Security Group ID
- Multiple EC2 instances can be linked.
We can refer to Security Group Rules.
Content
Create Security Group
- Go to the Amazon EC2 console.
- In the left-hand navigation bar, select Security Groups.
- Select the
Create security groupbutton.
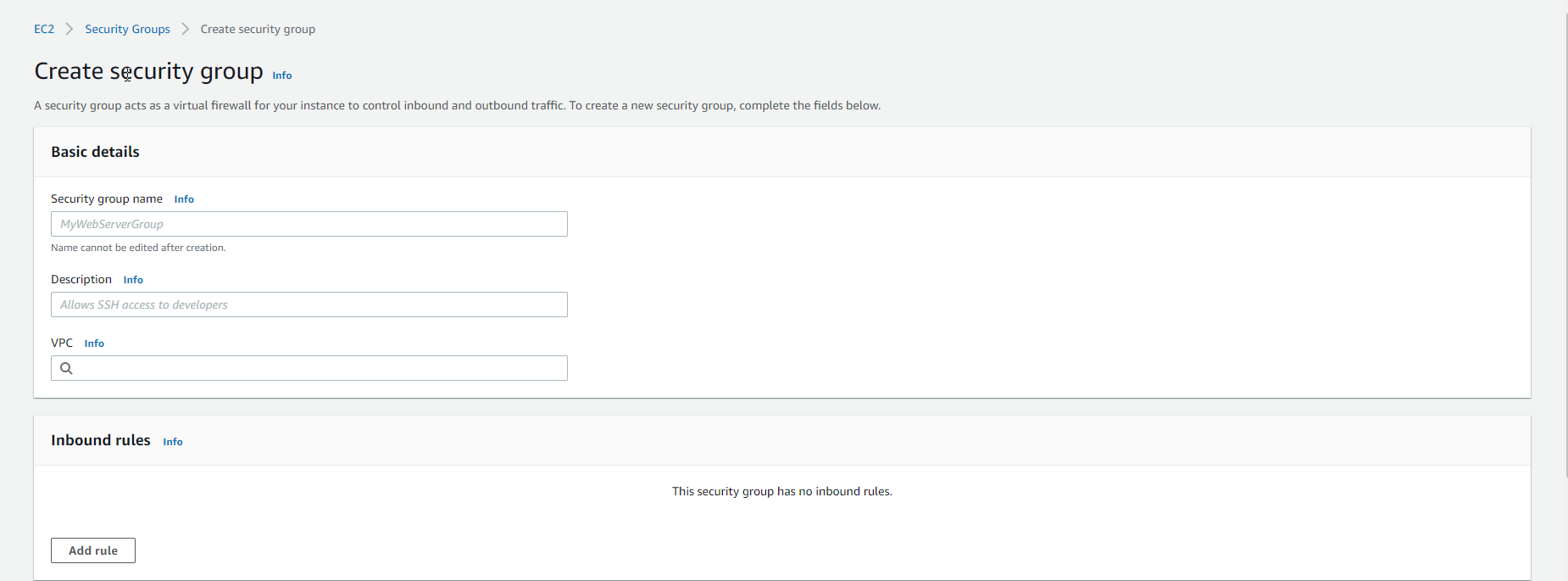
- In the Basic details section, we need to enter a name, and description and select VPC.
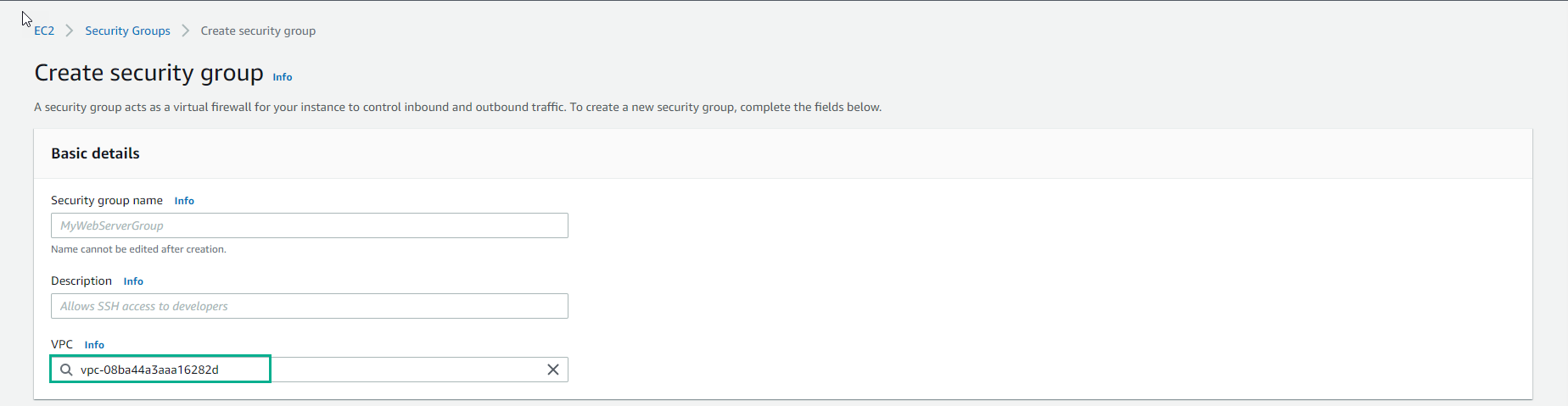
- In the Inbound rules section, click the
Add rulebutton to proceed further as follows:
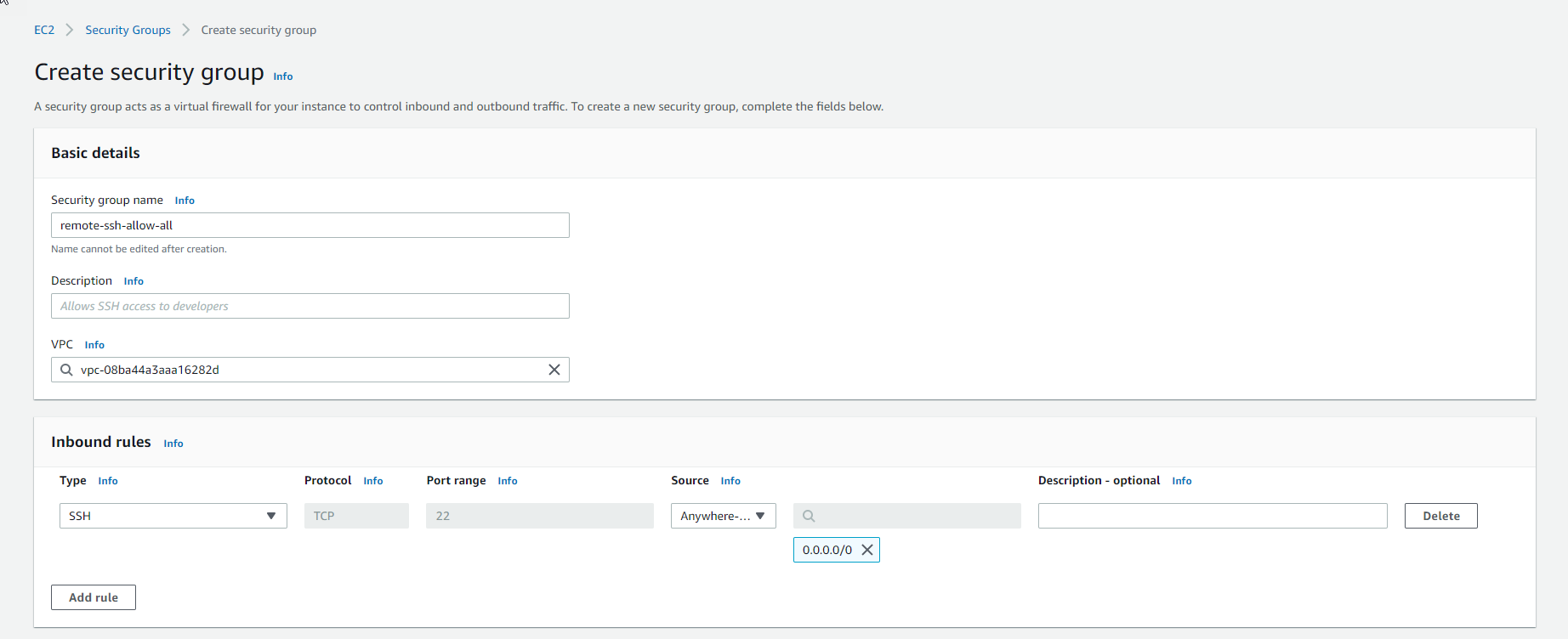
- In the Onbound rules section, we will keep the default.
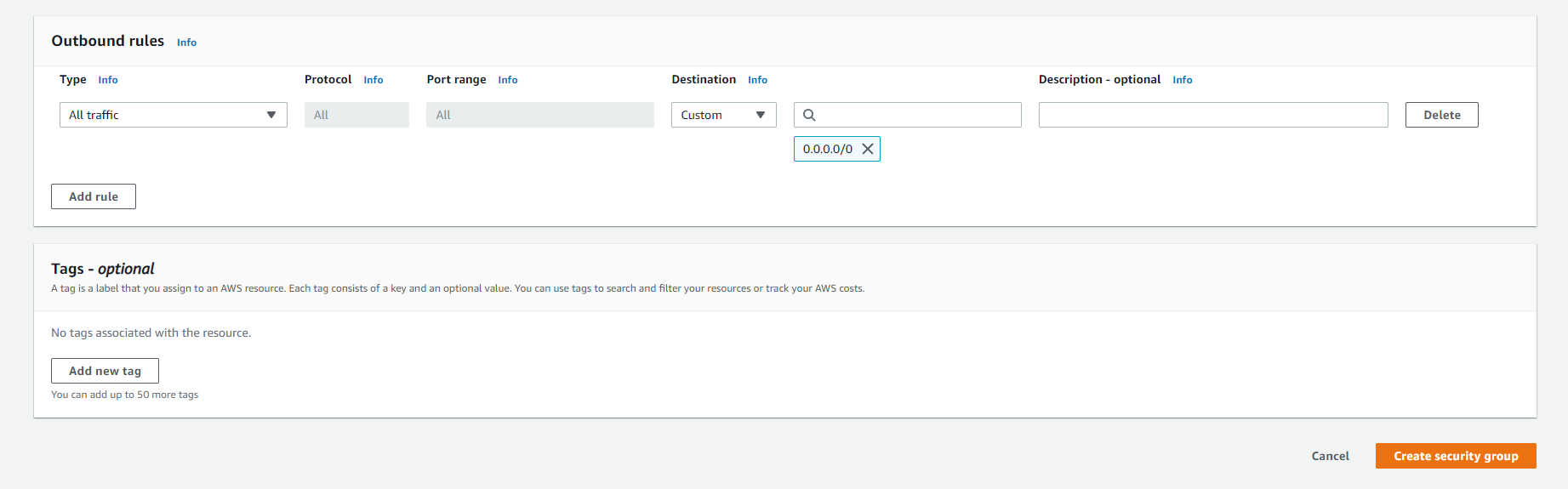
- In the Tags section, click the
Add new tagbutton to add specific Tags. - Click the
Create security groupbutton to initialize.
Alternatively, we can initialize via AWS CLI.
Best Practices
AWS recommends several standards as we proceed to use Security Groups. Securing these standards in a large system as well as multiple environments on the AWS Cloud is always a challenge, as new application deployments become faster and more frequent.
- Delete unused security groups
If a large number of unused security groups still exist, this can make it difficult for Administrators to manage and find, the configuration process can lead to errors due to some duplicate rules.
| Ingredients | Details |
|---|---|
| AWS Resources | Amazon EC2 security group |
| AWS Config Managed Rule | ec2-security-group-attached-to-eni |
| Criteria in PCI DSS | PCI.EC2.3 |
| Level in PCI DSS | LOW |
- Limited to Edit
Editing the Security Group is very important, just a small mistake can affect the whole system. Then we proceed to limit through IAM service and only some IAM Roles are allowed to perform editing operations.
| Ingredients | Details |
|---|---|
| AWS Resources | Amazon EC2 security group |
| AWS Config Managed Rule | iam-policy-no-statements-with-admin-access |
| Criteria in PCI DSS | PCI.IAM.3 |
| Level in PCI DSS | HIGH |
- Track creation and deletion
This has always been one of the most basic criteria for tracking activities related to the creation or deletion of Security Groups.
| Ingredients | Details |
|---|---|
| AWS Resources | Amazon EC2 security group |
| AWS Config Managed Rule | N/A |
| Criteria in CIS Benchmark | 3.10 |
| Degree in CIS Benchmark | LOW |
- Don’t forget to limit Outbound
We should always limit access to the Outbound side of a Security Group to specific Subnets.
| Ingredients | Details |
|---|---|
| AWS Resources | Amazon EC2 security group |
| AWS Config Managed Rule | vpc-default-security-group-closed |
| Criteria in PCI DSS | PCI.EC2.2 |
| Level in PCI DSS | MEDIUM |
- Limit the range of Inbound Ports allowed to access
Only Ports required for the operation of an application should be considered open on the Inbound side of a Security Group. With a large number of unnecessary ports open, this can lead to potential vulnerabilities that are easily exploited by exploratory access as well as attacks.
| Ingredients | Details |
|---|---|
| AWS Resources | Amazon EC2 security group |
| AWS Config Managed Rule | restricted-ssh, [restricted-common-ports](https://docs.aws.amazon.com /config/latest/developerguide/restricted-common-ports.html) |
| Criteria in CIS Benchmark | 4.1, [4.2](https://docs.aws .amazon.com/securityhub/latest/userguide/securityhub-cis-controls.html#securityhub-cis-controls-4.2) |
| Degree in CIS Benchmark | HIGH |
| Criteria in PCI DSS | PCI.EC2.5 |
| Level in PCI DSS | HIGH |
Enable AWS Config Service
Organizations and businesses should urgently address those challenges through automated control and monitoring tasks. With the AWS Config service, we can configure many rules to automate the detection of violations to the current system.
Enabling the Config service will be the premise for the next part of the exercise.
Here are a few steps to a basic Managed Rule configuration.
- Access the service Config
- If it is the first time accessing the service, they press the
Get Startedbutton. - In the Settings section, keep the default configuration as follows:
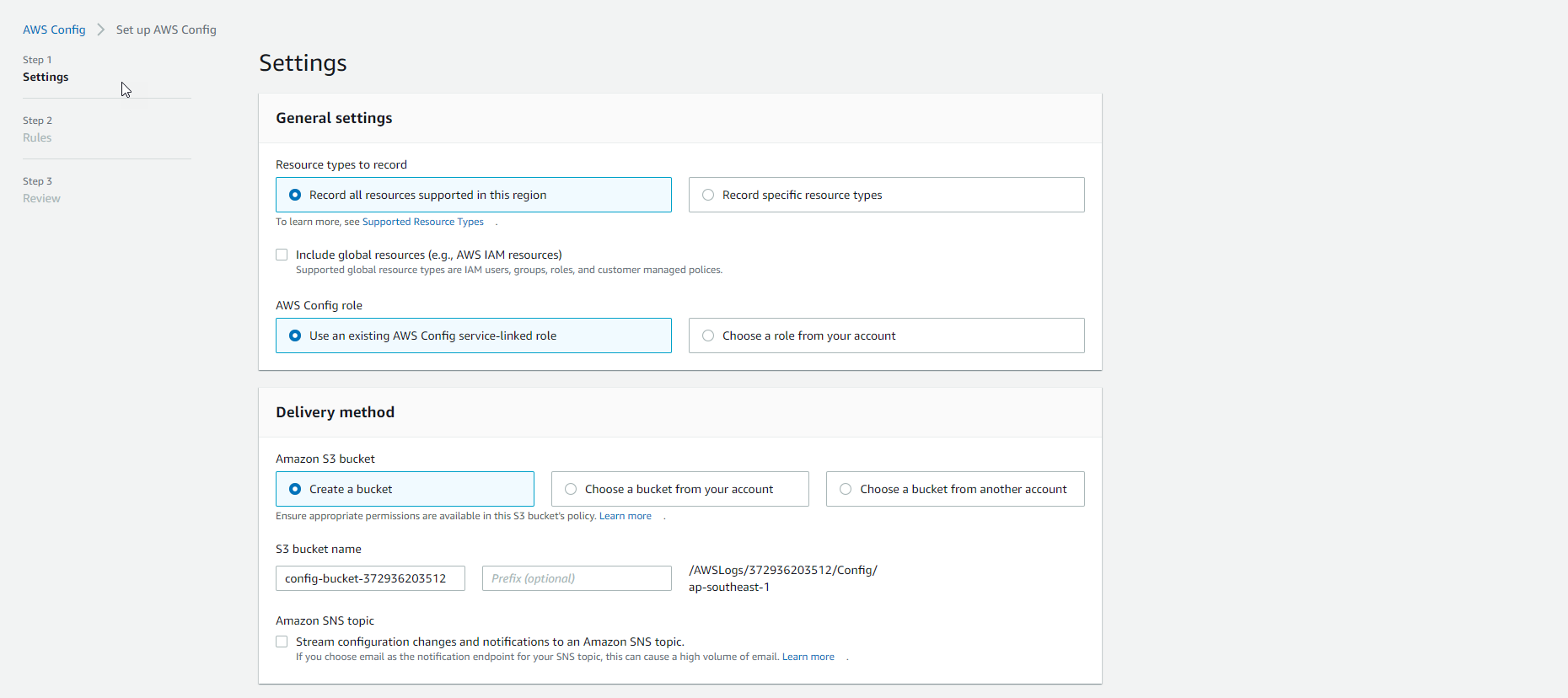
- In the Rules section, we see a list of Managed Rules.
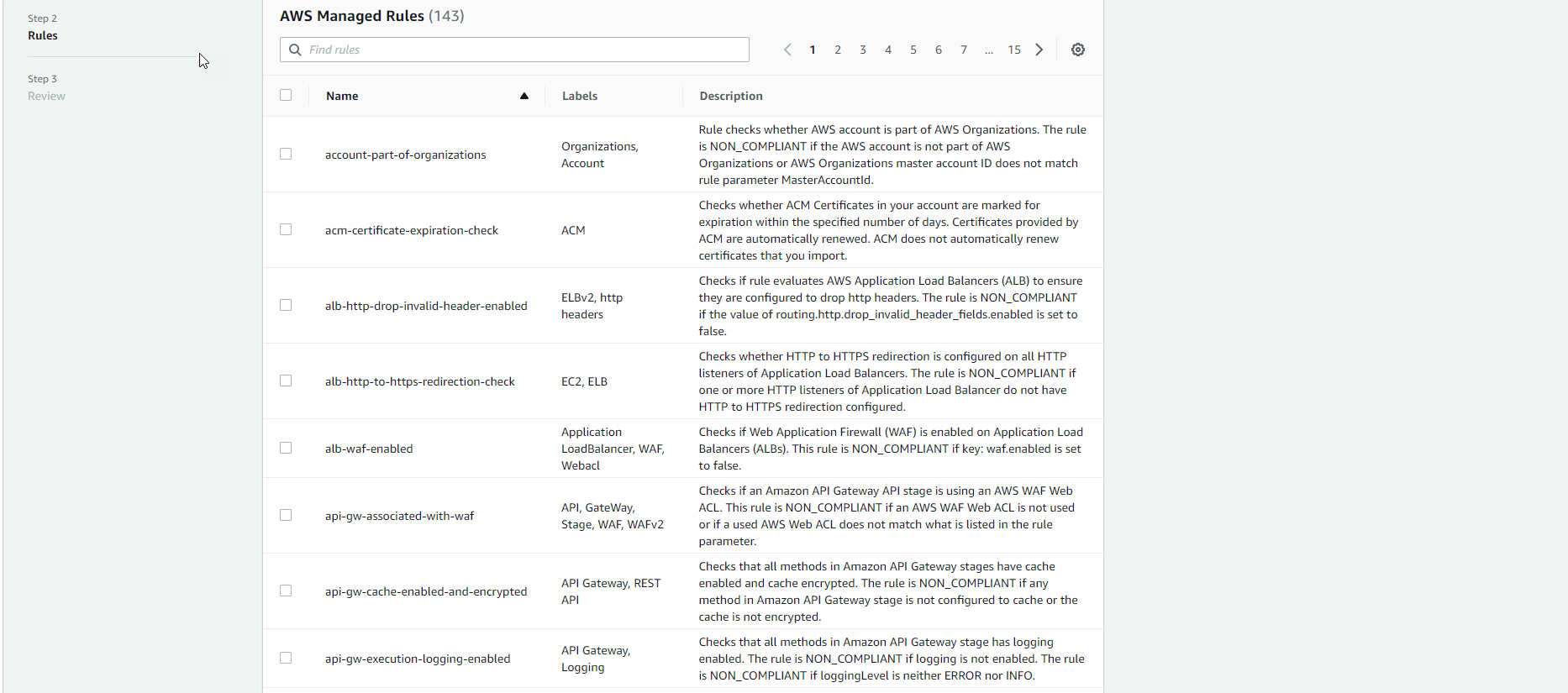
- In the search box, enter
restricted-sshand select the corresponding rule.
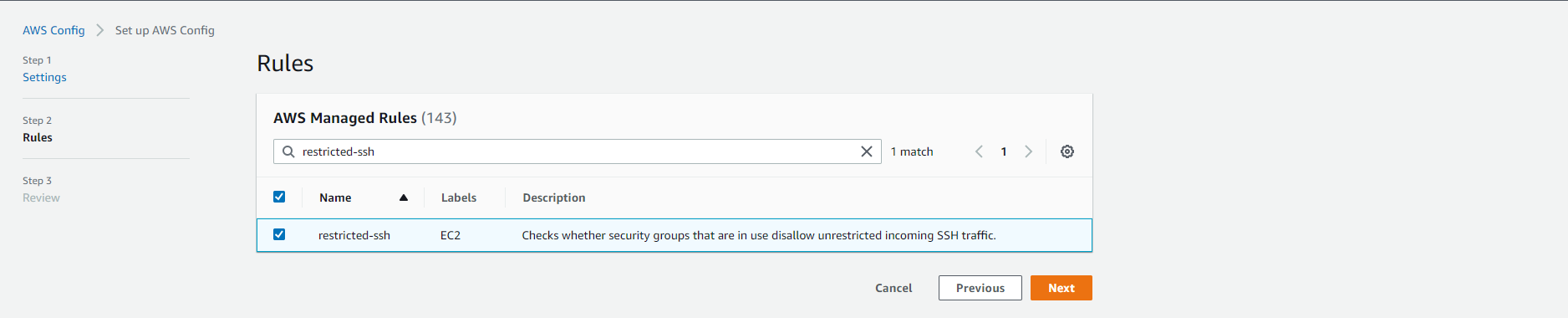
- Conduct initialization.